Background:
Recently I configured Citrix Products (XenApp, XenDesktop, PVS) and Horizon View Products (View, Hosted Application, App-Volume, UEM) to my home lab.. I have only one external IP address (Thanks to Comcast that they do not change external IP frequently any more.) and would like to access both environments remotely. After researching through internet and support from Carl Stalhood (very nicely written blog for NS.) I was able to configure NetScaler as an external gateway into my lab environment.
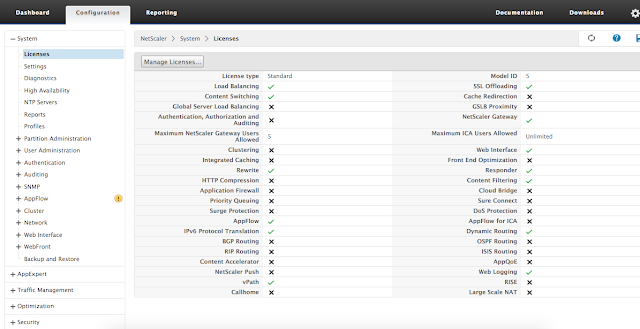
Below is the configuration for my Citrix NS VPX Express edition v11.
Before you begin I would recommend a wild card certificate, for me it was very necessary so I bought it from Comodo for $75.
See Carl Stalhood blog for in detail NS configuration and SSL/CSR request and installation.
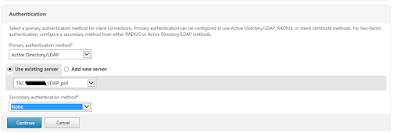
I do have two factor authentication using two different vendors (Duo Security and WiKID -will write blog on next) for my Horizon View and Citrix environment.
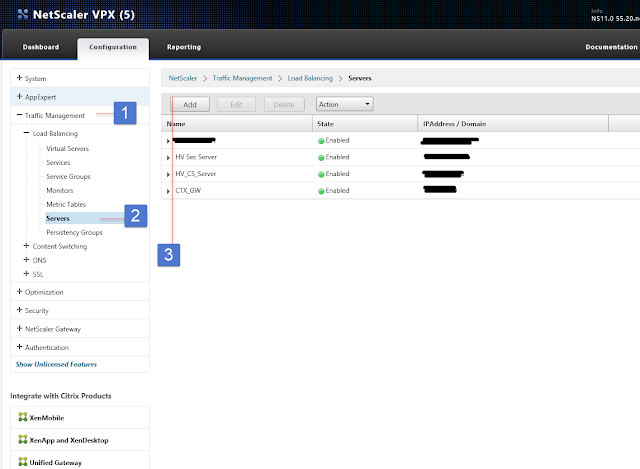
Once the initial configuration and license configuration is configured next step is to setup LDAP server and policy. To do this click on System > Authentication>LDAP>Server to add new server.
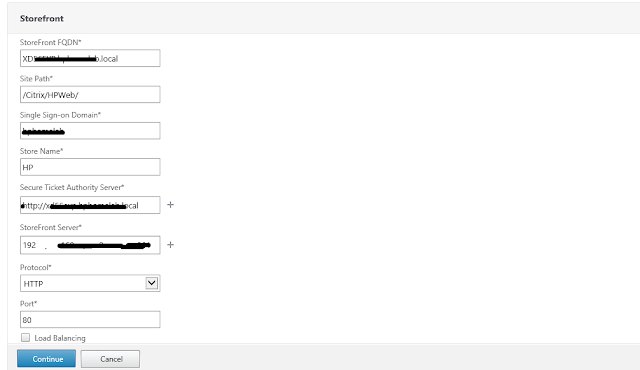
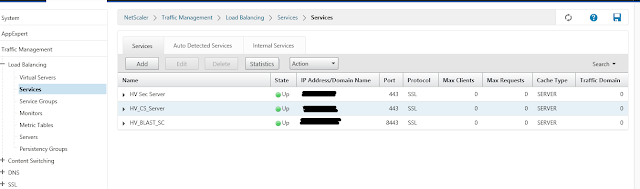
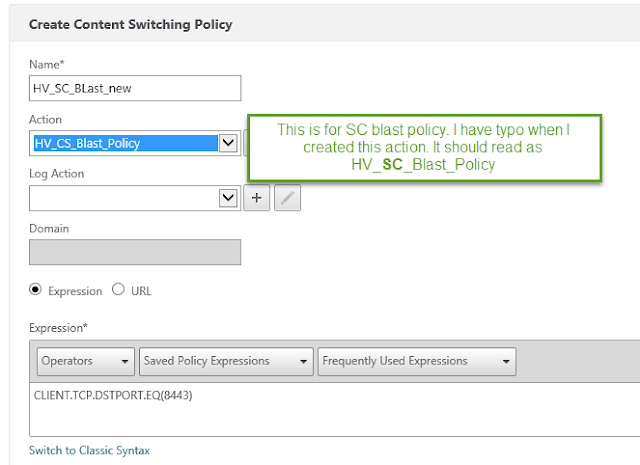
Create the same policy for the Connection server and one for blast.
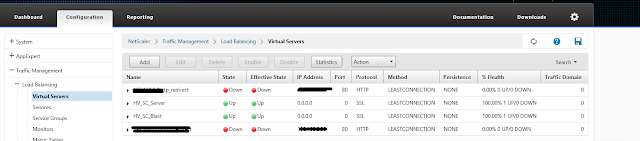
Next you need to configure the Action and content switching policies. Todo this select Traffic Management > Content Switching > Actions
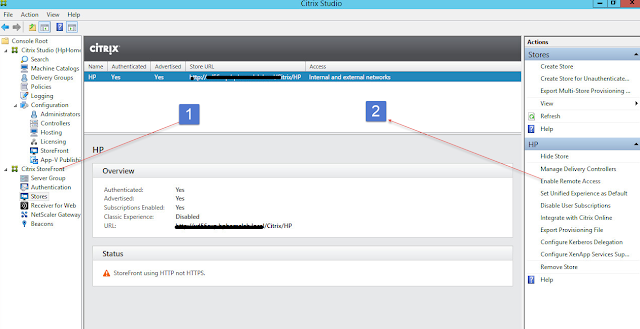
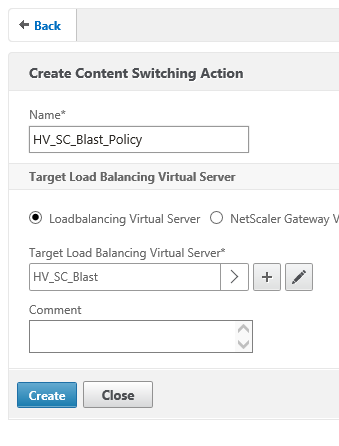
As you can see on below picture I already created two action policies one for Security Server – Blast and one for CS server.
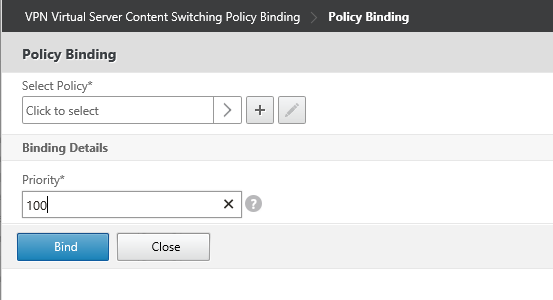
To create policy Click Add and type the policy name and select the Virtual server from the drop down for that policy.