Many customers are moving towards extending their Datacenter workloads to the clouds, and Microsoft Azure is one of the partners that the VMware EUC team works very closely with. VMWare Unified Access Gateway, what we called “UAG,” is available in the Azure AD app gallery directly, reducing and simplifying the efforts of integration and configurations.
The other main benefit aside from Cloud deployment we gain from the integration is we can now leverage g Azure AD conditional access policies applied to UAG for Horizon use cases.
In my setup, I have my domain federated with the ADFS environment. The workflow would be when the user accesses my Horizon View external URL. They will be redirected to Azure AD for auth. Since my domain is federated with ADFS, It will redirect my users to ADFS based on the ADFS auth policies user will authenticate at ADFS. Still, additional policies can be applied at the Azure level, such as leveraging Azure MFA, Trusted location, browser, or device registered policy can be added.
Let’s dive into the configuration. I will divide this into a three-part configuration.
- Azure AD configuration
- UAG Configuration
- Connection Server Configuration
Azure AD Configuraiton
First, you need global or Application Administrator rights. Application Administrator rights will suffice to add UAG as an app and granting user rights. If you want to apply any additional conditional access policies, you need to have Conditional Access Administrator rights.
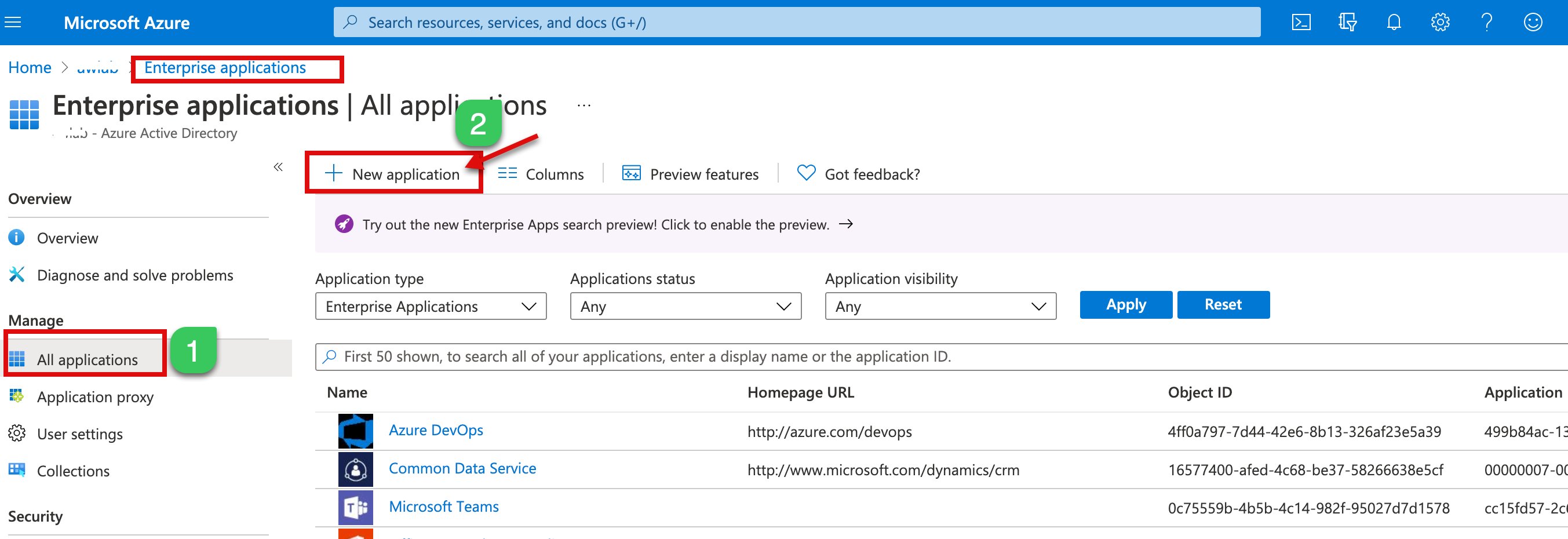
1a. Login to your Azure AD Portal and navigate to Application blade here or using the below link.
https://portal.azure.com/#blade/Microsoft_AAD_IAM/StartboardApplicationsMenuBlade/AllApps/menuId/
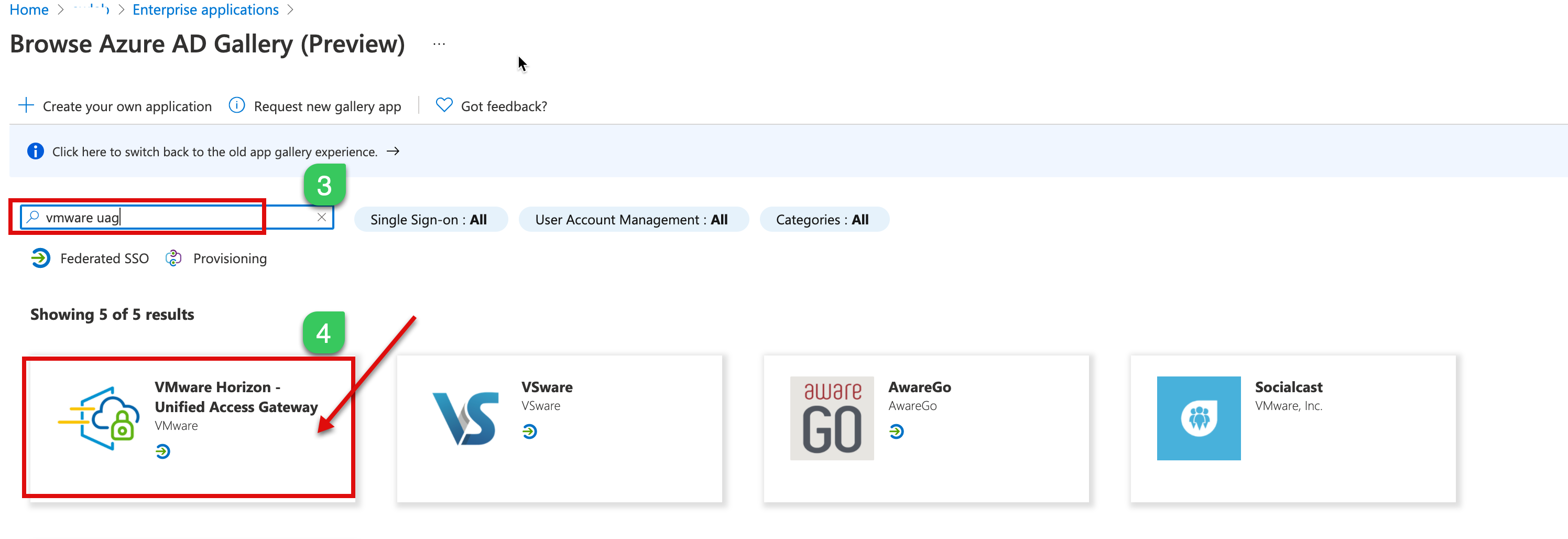
1.b After login, click on New application, search for “VMware UAG,” and Select VMware Horizon Unified Access Gateway from the results
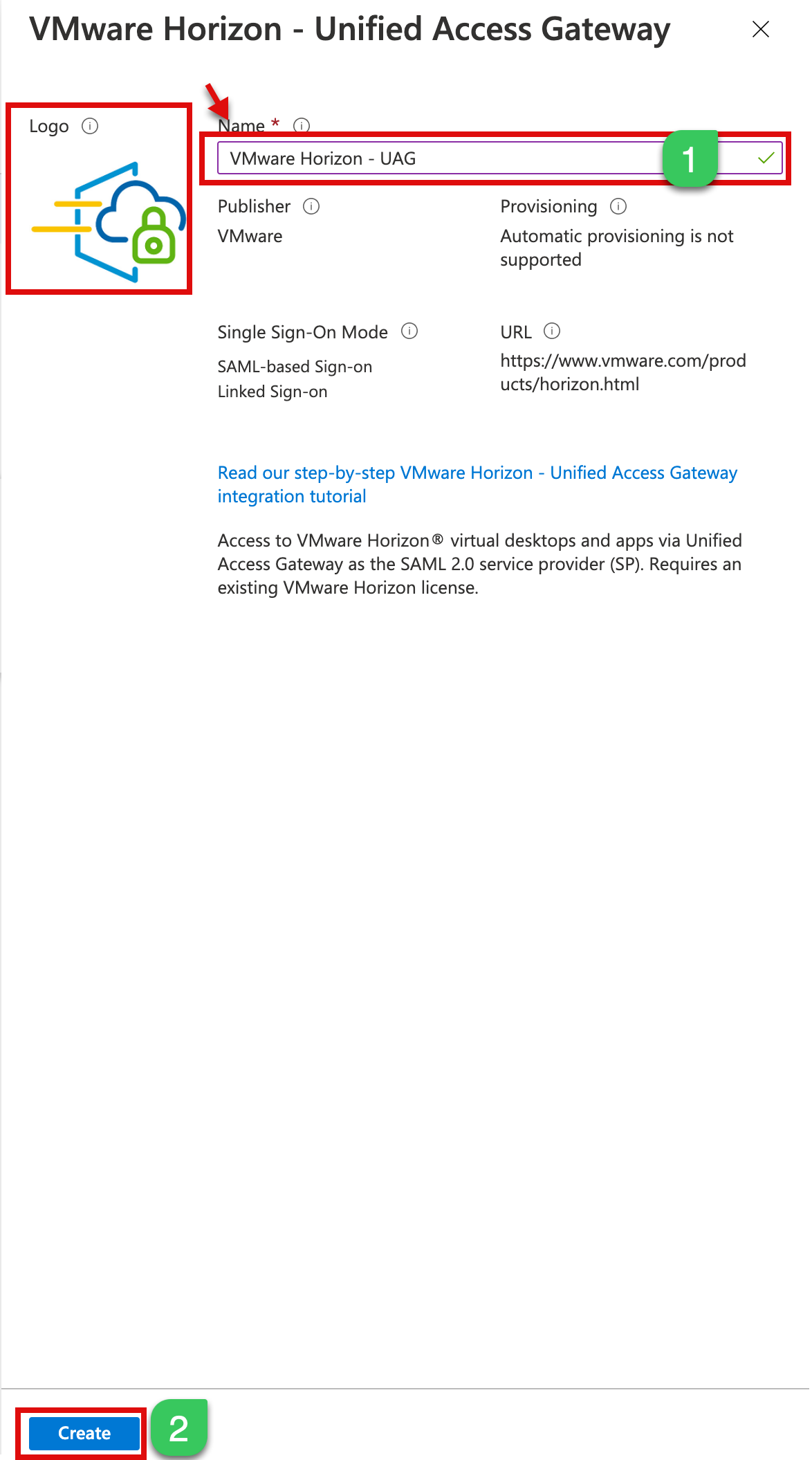
1c. In the next step, Type your preferred Name of this configuration, I call it – “VMware Horizon – UAG,” and Create a new app. You can also change the Logo later, and you can configure the other SAML configuration on the next part.
1d. In the next step, we will now configure SAML via option Single sign-on to the application.
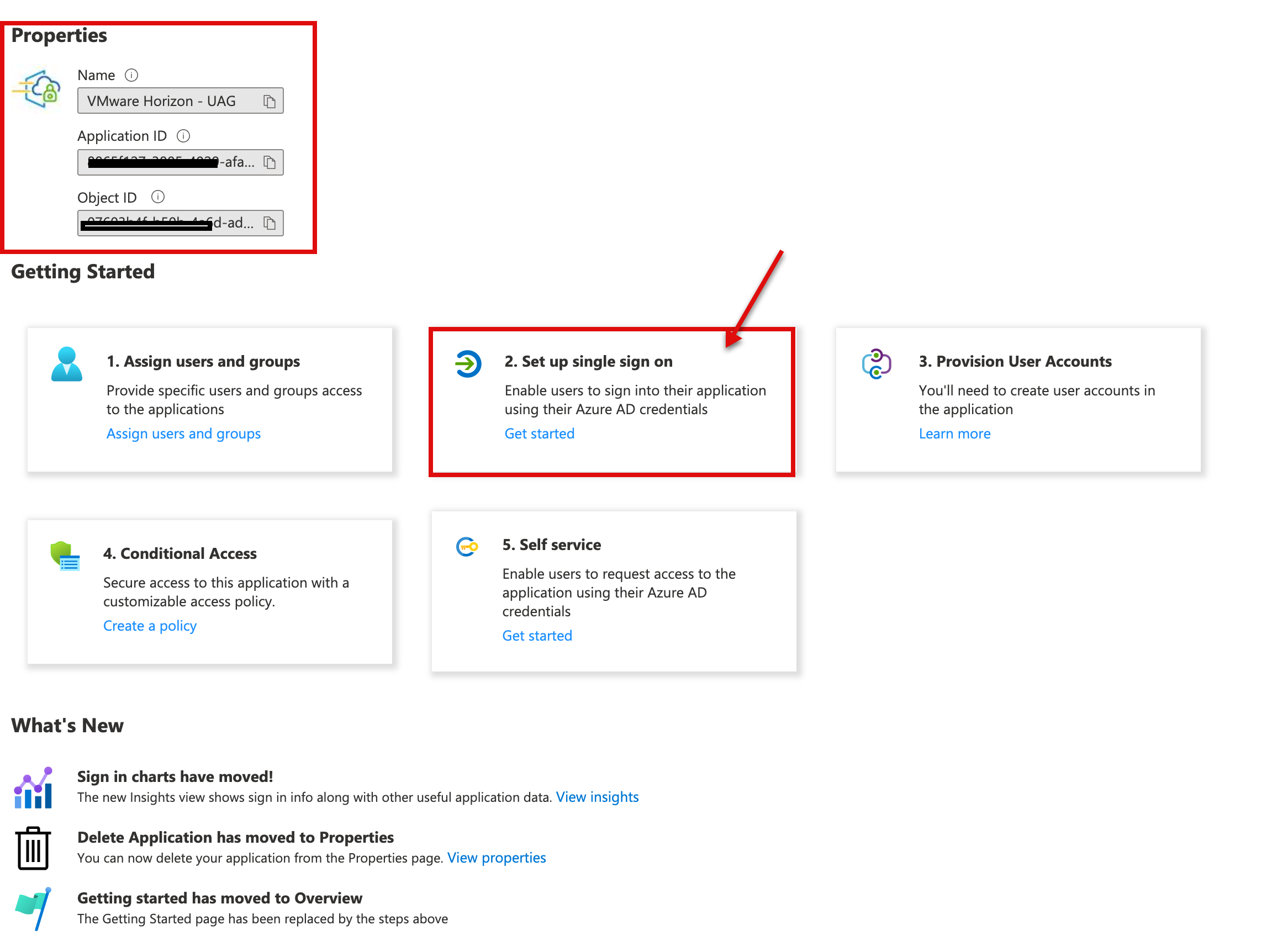
1e. In the next step, select SAML from the single sign-on method.

1.f On the Set up Single Sign-On with SAML page, select edit on Basic SAML Configuration.
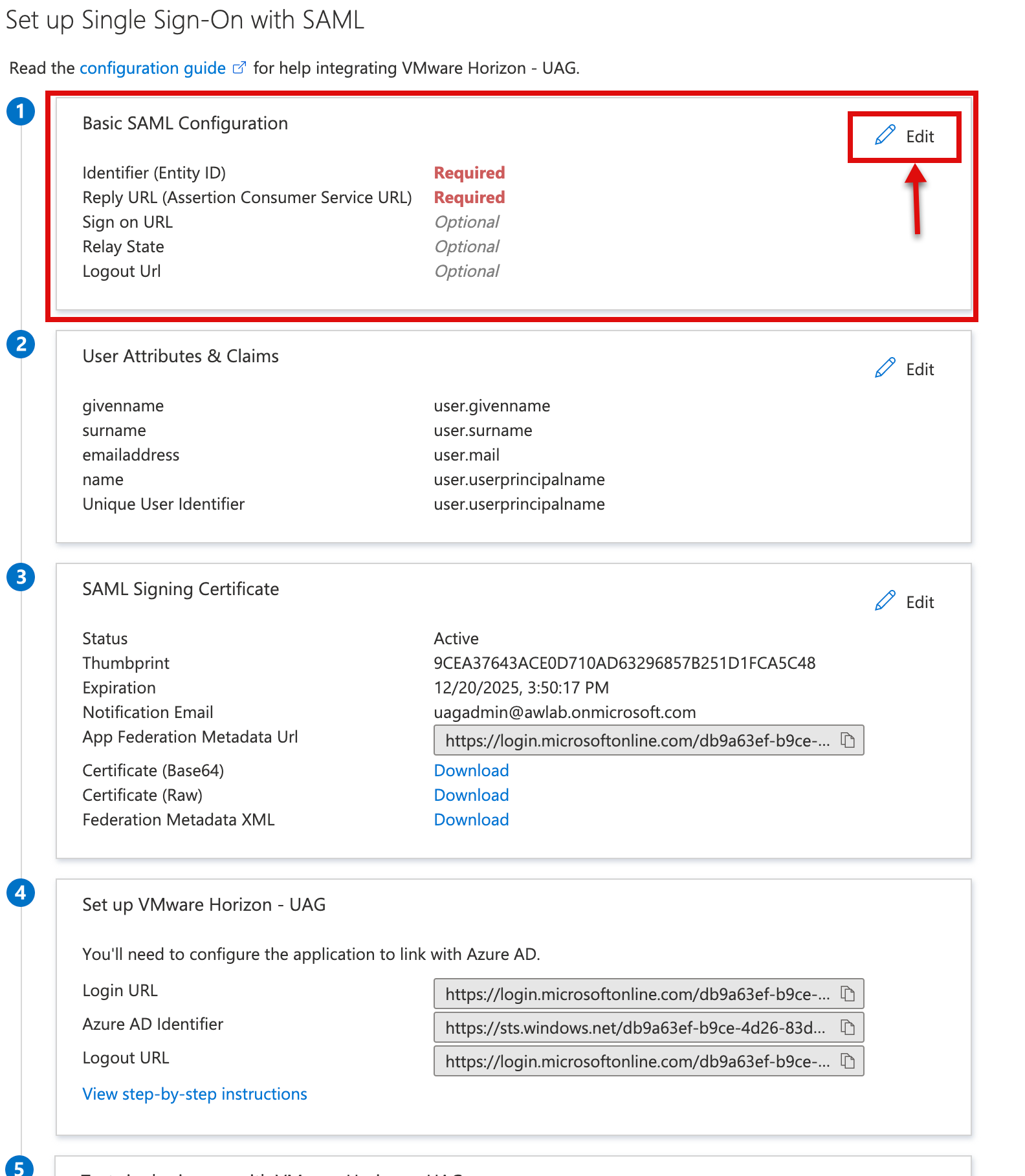
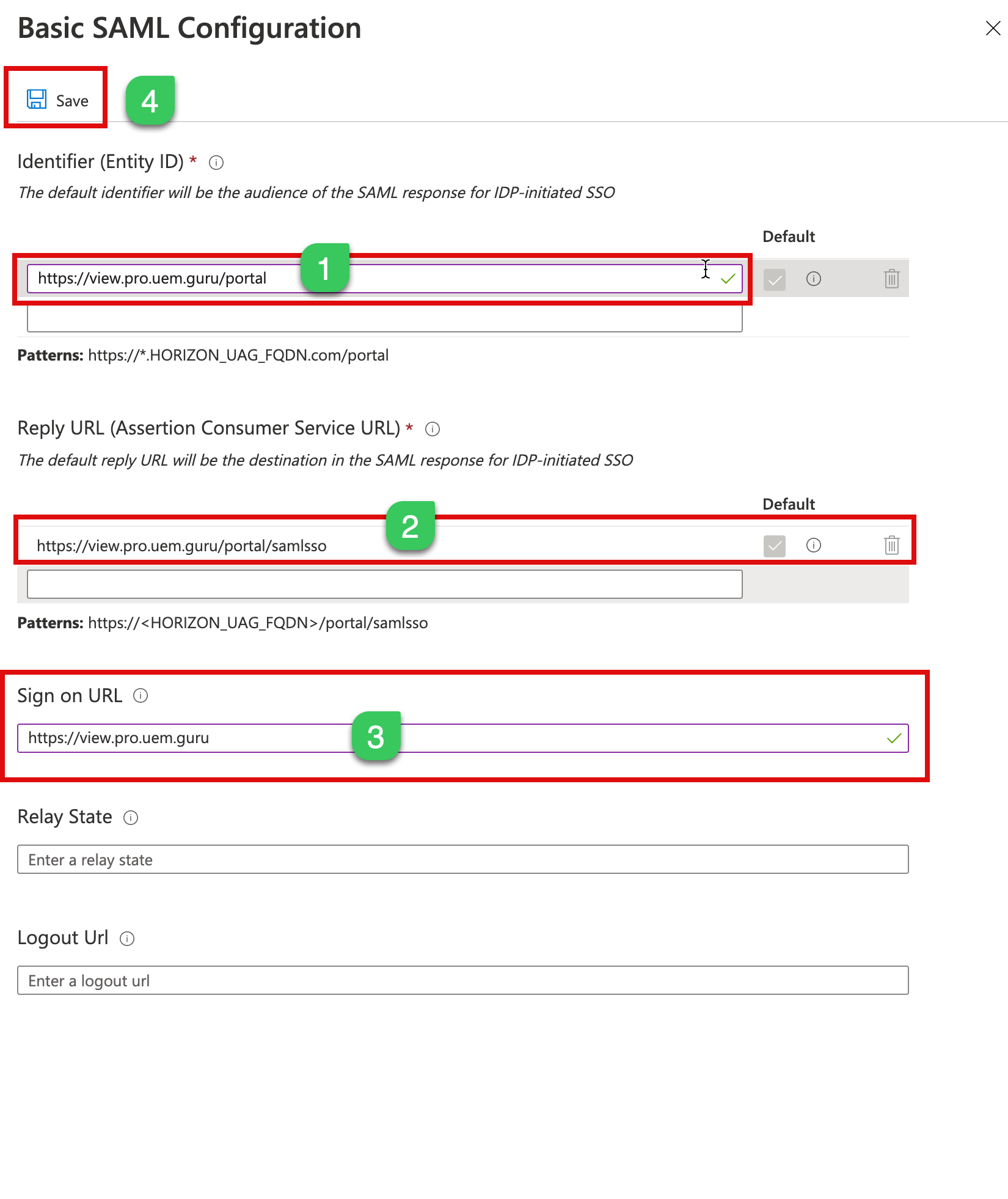
1g. In the next step, type as below and click save
Identifier (Enitity ID)* https://UAGExternalFQDN/portal
Reply URL: https://UAGExternalFQDN/portal/samlsso
Sign-on URL: https://UAGExternalFQDN
Please make sure you check the Default checkbox for Identifier and Reply URL.
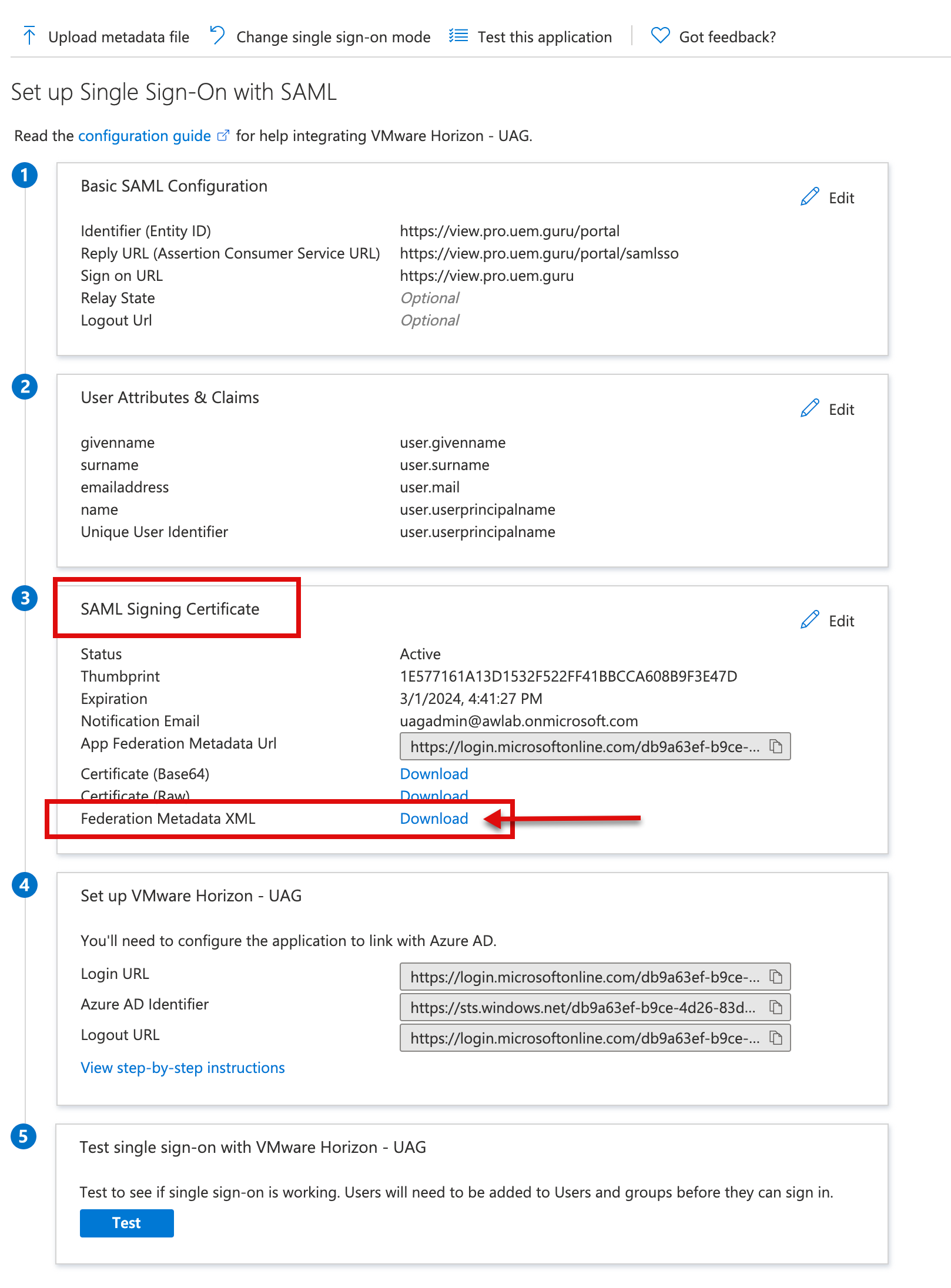
1h. In the next step, download the Federation Metadata XML; later, we will upload this XML into UAG.’s
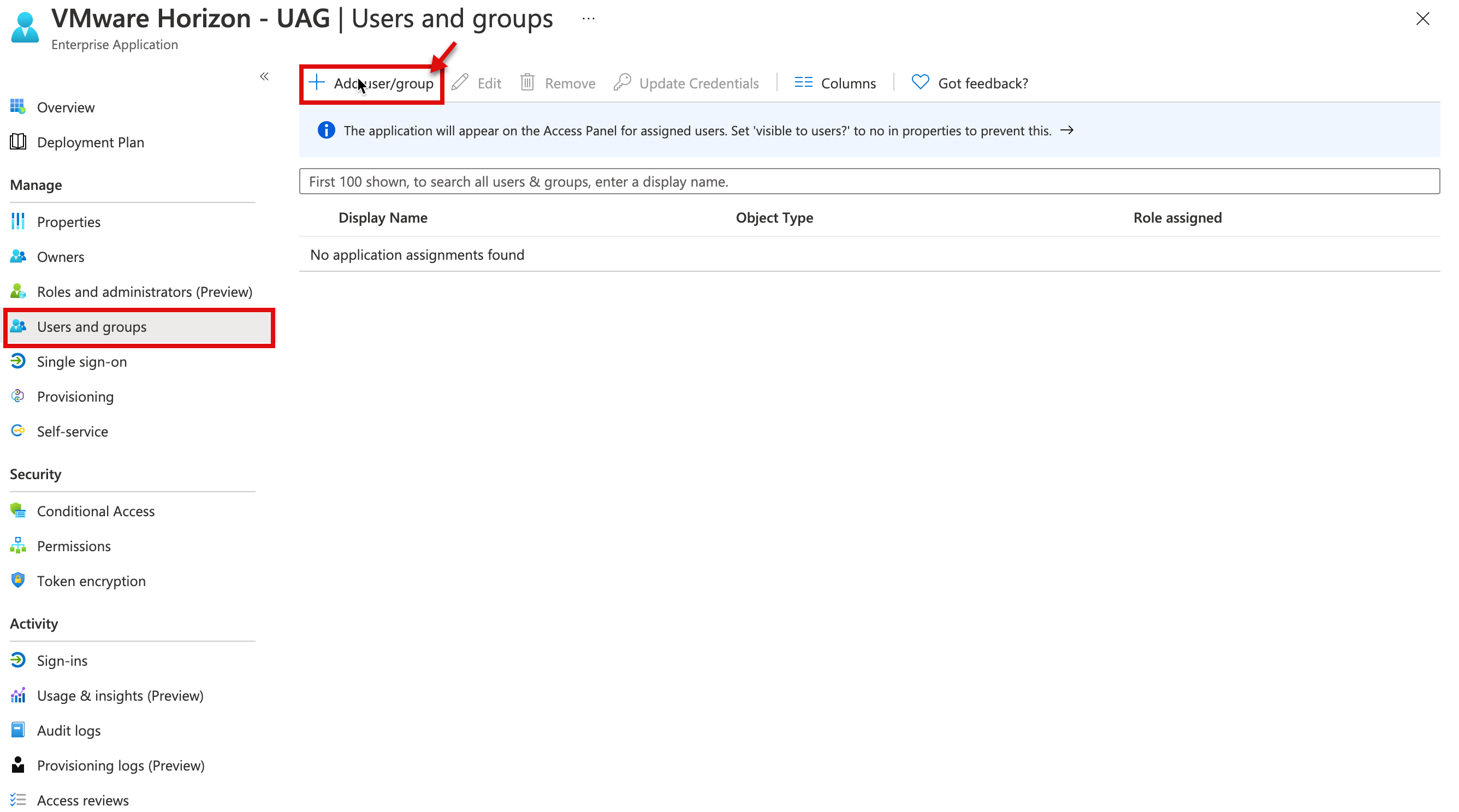
1i. Now, we will assign users who can access this app, Close the SAML config option and select “Users and groups” from the left menu side and click on Add user/group. I will grant access to “VDI Group” and “RDSH Group” security groups in my environment.
1j. Let’s find users group and In the next step, type as below and click select and assign.
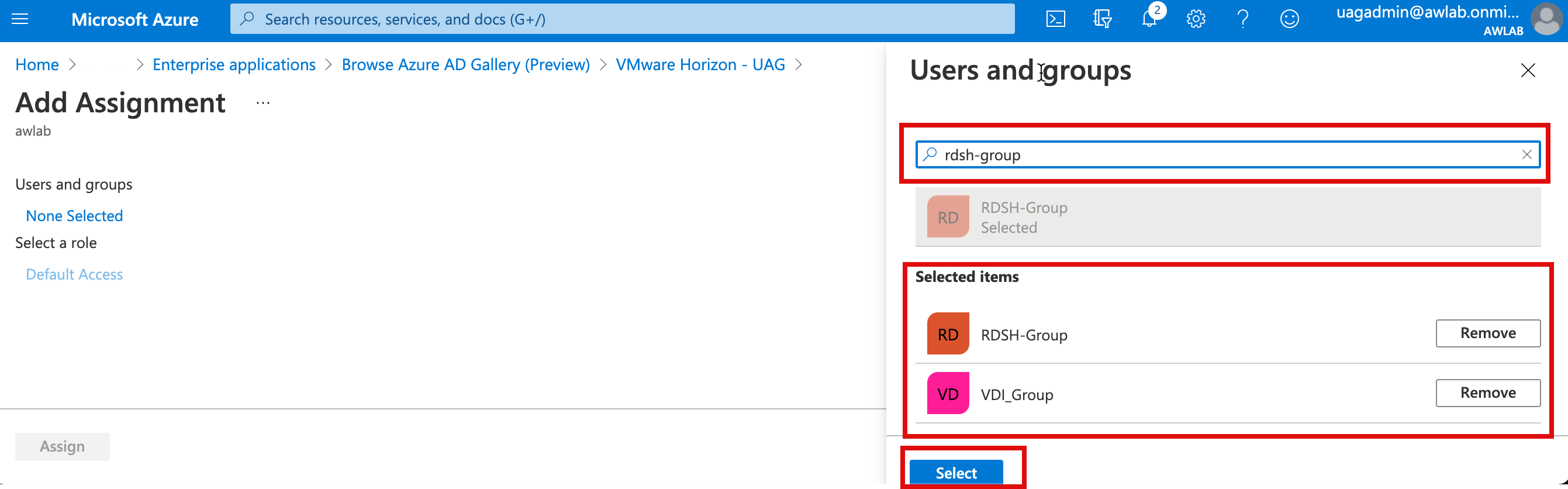
1k. At this step, we have completed configuration on the Azure side; if you have a requirement to configure the conditional access for a more granular policy, you can select conditional access policy and apply various conditional policy specific to this UAG-Horizon app, such as MFA, User, and Sign-in risk score, or Device platform. I will post a blog in the future to cover some more specific use cases.
In part 2, we will configure the SAML in UAG and the connection server for TrueSSO.
UAG Configuration
This section will configure the SAML configuration for UAG; in my lab setup, I already configured the Horizon Edge setting for UAG and verified using the Username/Password option works. I would advise doing the same before you configure the SAML to make sure the initial configuration is set up correctly and then change the setting to SAML only.
We will first upload the metadata.xml file downloaded from above step 1h and upload it into UAG’s Identity Bridging settings. If you have multiple UAG’s you have to do it manually for each UAG’s in your setup.
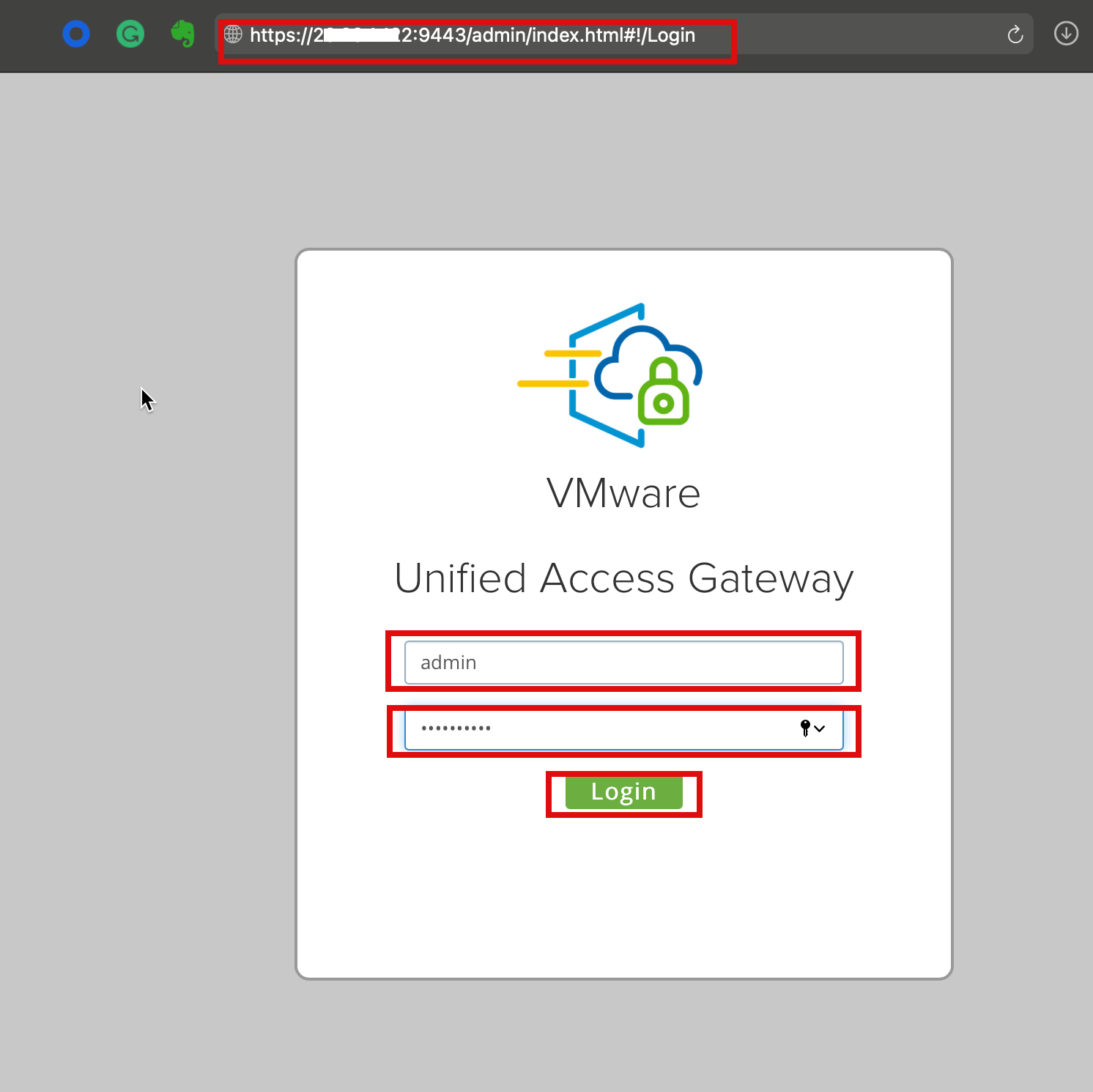
2a. Log in to UAG’s admin portal using https://fqdn or IP address of UAG:8443/admin# and use admin credential to log in; once loging select Configure Manually
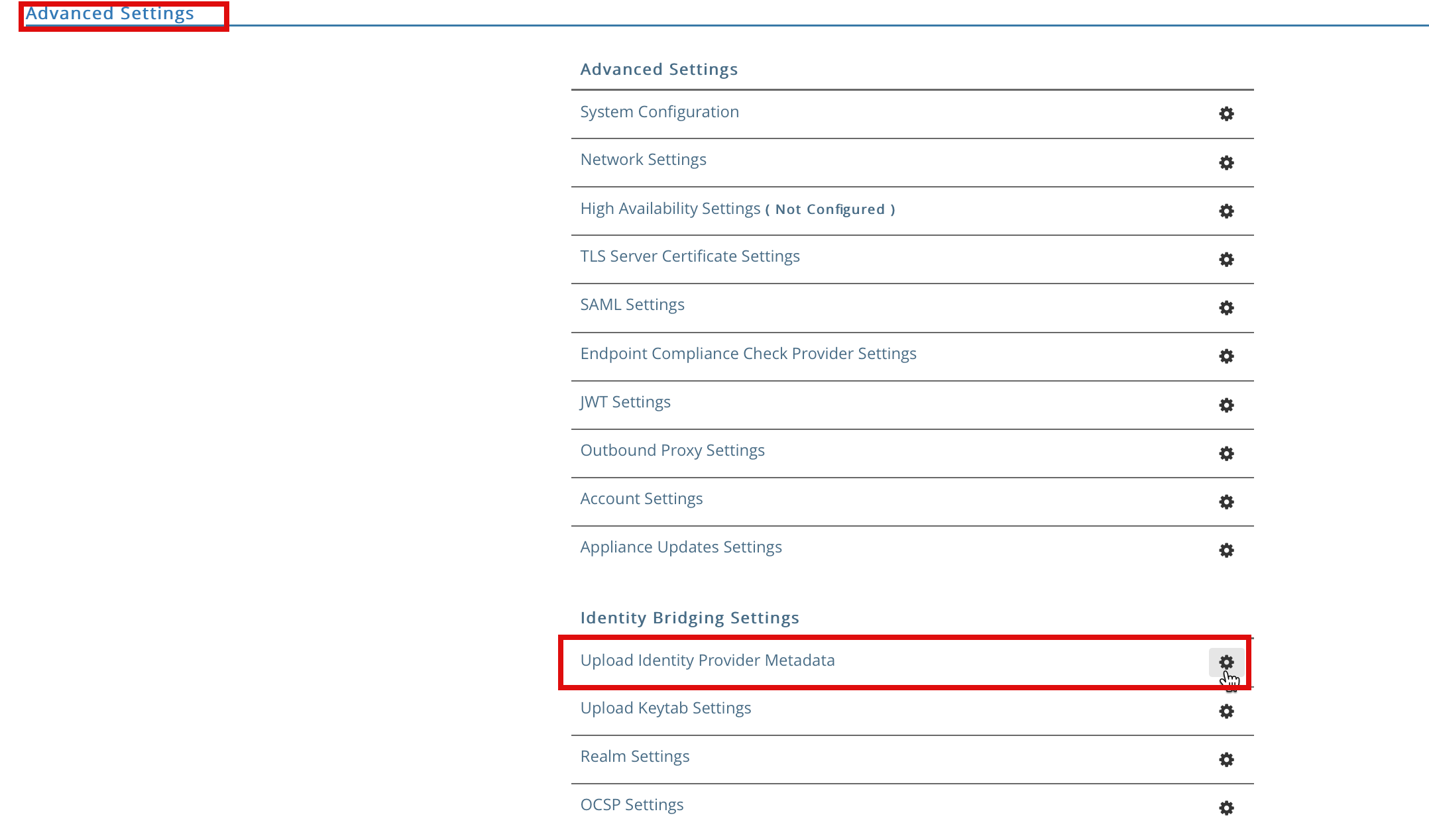
2b. Next, let’s upload metadata.xml from Step xx to the IDB settings section, select “Upload Identity Provider Metadata gearbox icon.
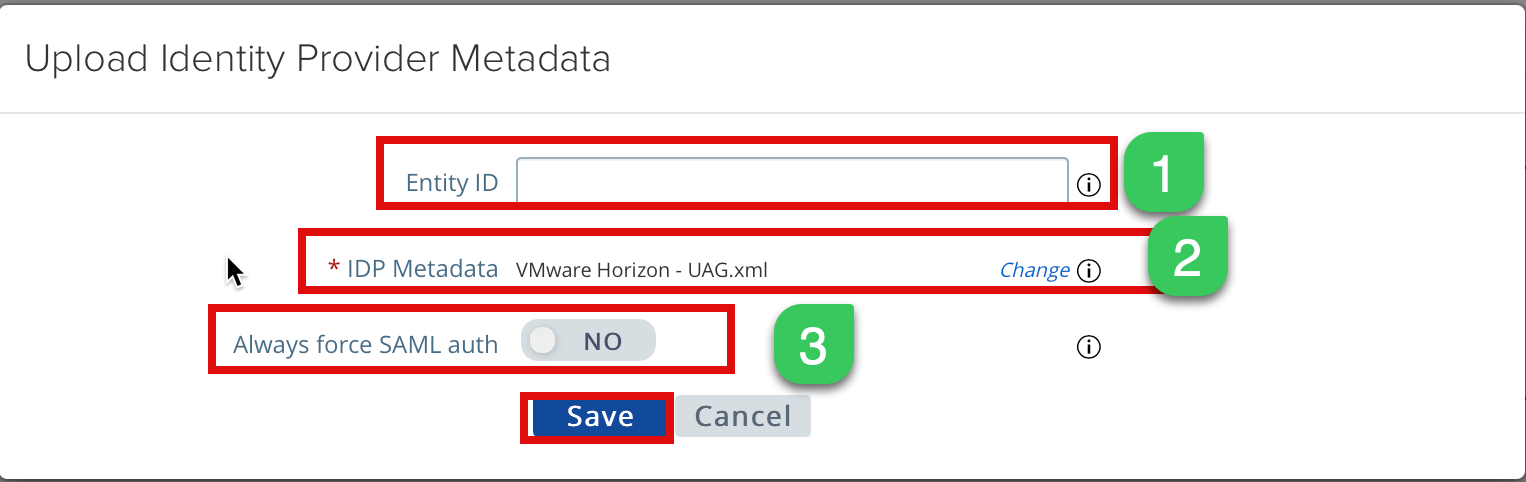
2c. Let’s upload the metadata file here and some other optional settings.
Entity ID: You can leave it blank, and it will parse the value from the metadata XML file
IDP Metadata: Browse the Metadata file you downloaded from step xx and upload it here
Always force SAML auth: If you enable this setting, it will require re-authentication of every login even if the client has a valid access token/cookies.
2d. Let’s update the Horizon edge setting for SAML; under the General Settings section, select show Edge Service settings and click on the Horizon Settings gear icon.
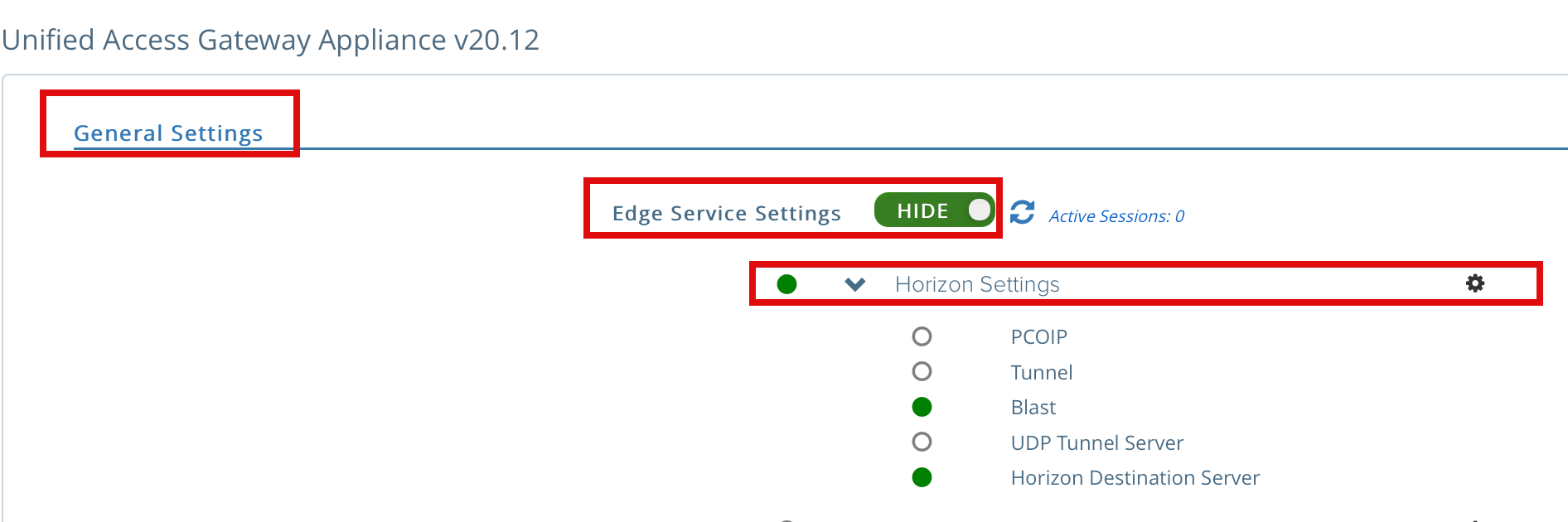
2e. Click More on the bottom of the Horizon Settings page to expand the page.
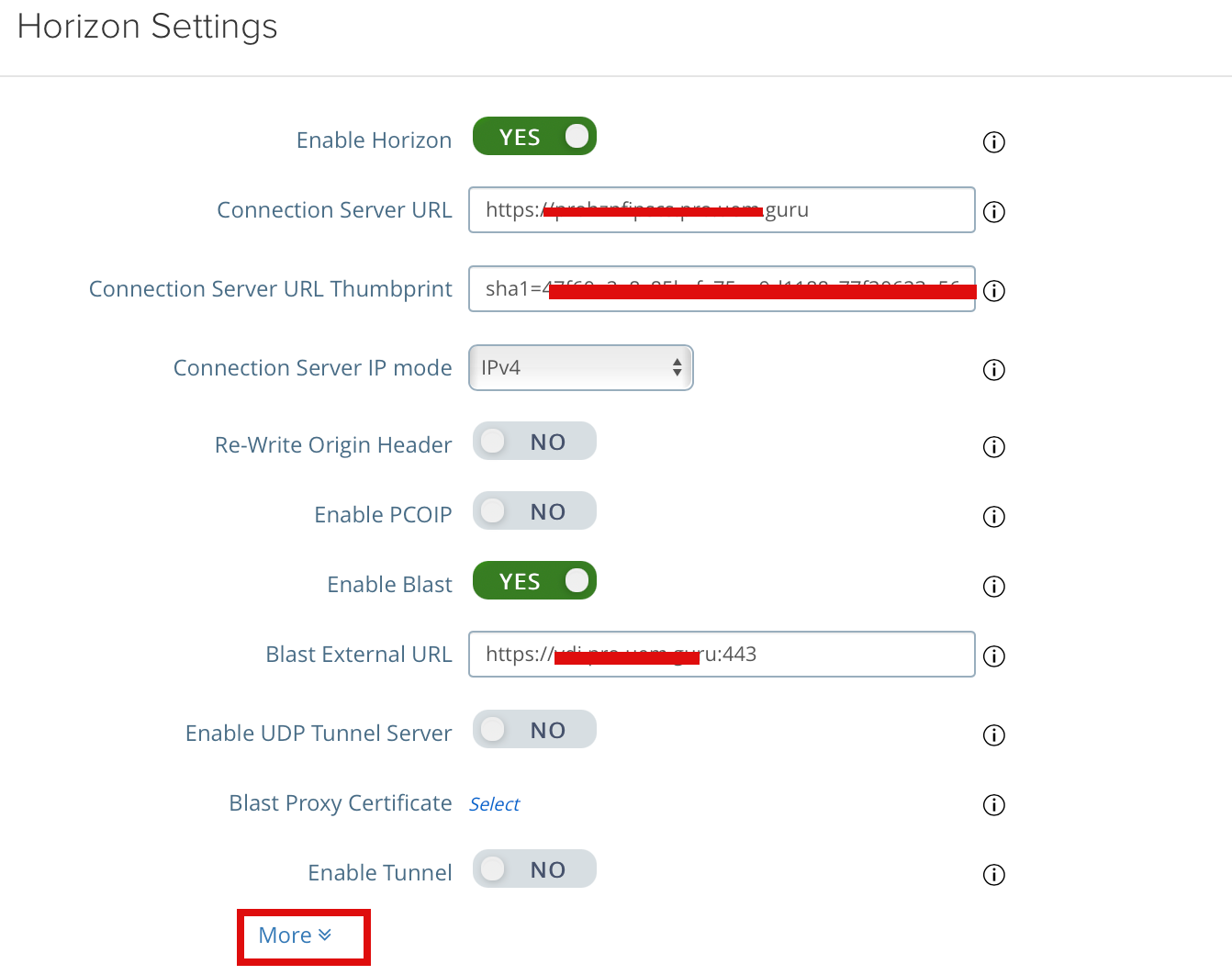
2f. In the Auth Method section configured as below
Auth. Methods: SAML ( You also have an option to SAML and Passthrough and SAML and Unauthenticated, In my use case, we will only allow SAML auth and no passthrough or unauthenticated access. I already configured TrueSSO in my lab, so I will select the only SAML; if you haven’t configured TrueSSO, you can use SAML and Passthrough)
Identity Provider: Select from the dropdown if you have uploaded multiple IDB XML files multiple XML files in Step 2c. you may have different IDP provider available
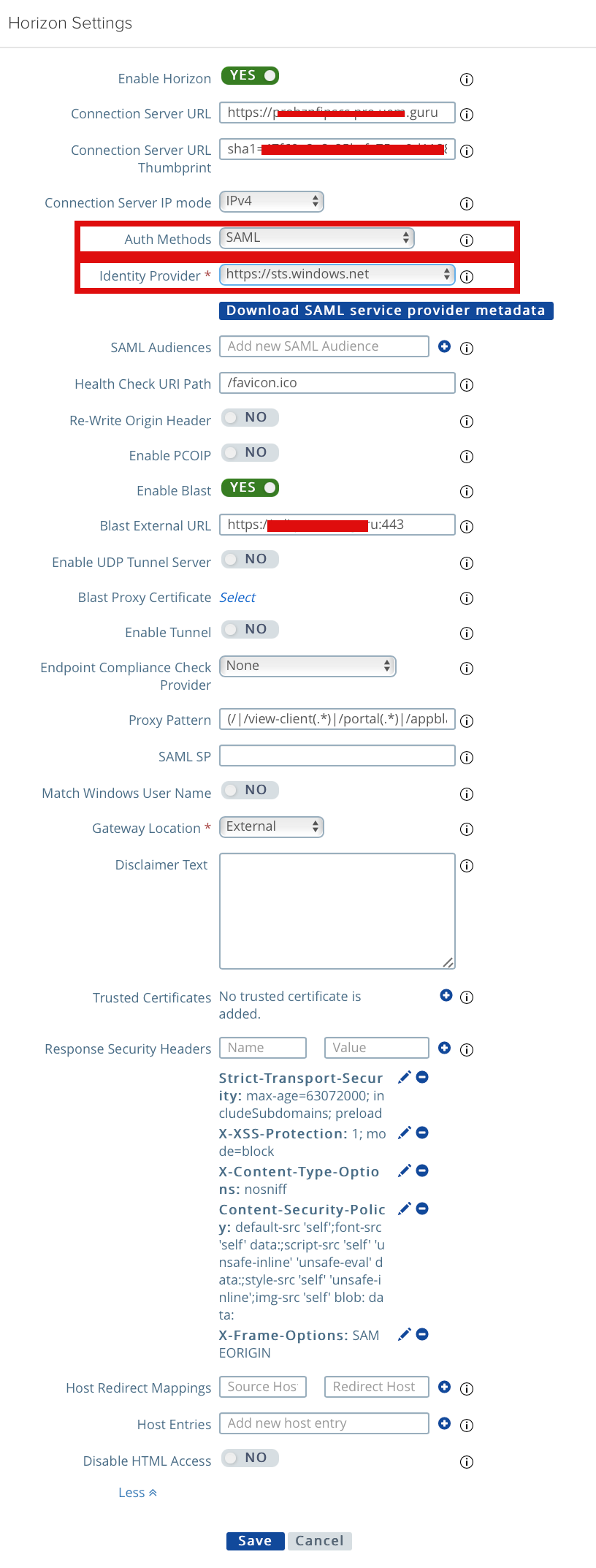
At this step, if you don’t have TrueSSO configured and you have chosen the auth method as SAML+Passthorugh, you can skip the below step. These are only required if you have configured TrueSSO and SAML only as Auth Method.
Configuring Horizon Integration with Microsoft Azure AD for True SSO
One of the benefits TrueSSO provides us is not requiring another password prompt when end-user access their virtual desktop or application, and provides a secure access end to end using passwordless authentication using a short-lived certificate. I will post a blog about TrueSSO in the future, but you can find out more using the link here.
TrueSSO can work with most SAML-based IdP; it does not require Workspace ONE Access. You can configure with Okta, Ping as well.
In my setup, I have two connection servers configured, so I have to configure the SAML authenticator for each instance; if you have multiple instances of the connection servers, you have to do the same.
3a. Log in to Horizon Admin console
3b. Configure Connection Server SAML settings for each instance. Navigate to Settings and select Servers > Connection Servers > Choose one of the connection servers from the list and Edit
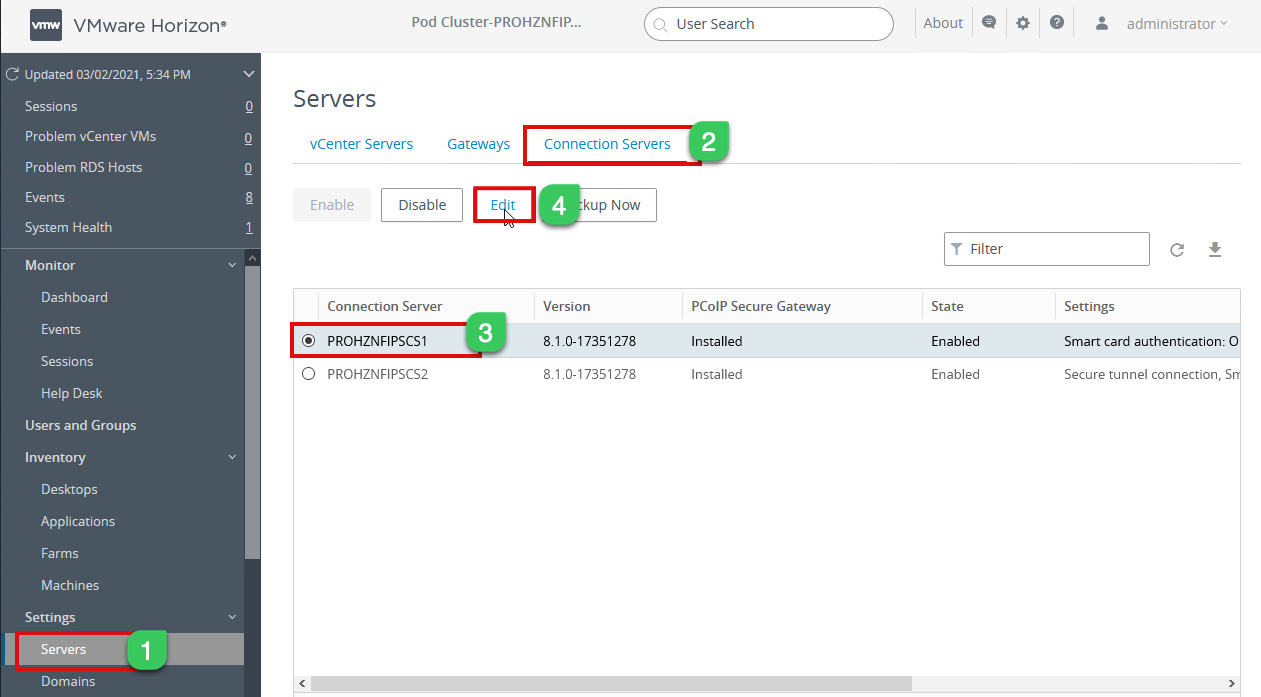
3c. Now select the Authentication tab, and under “Delegation authentication to VMware Horizon,” Select Required and click on Manage SAML Authenticators
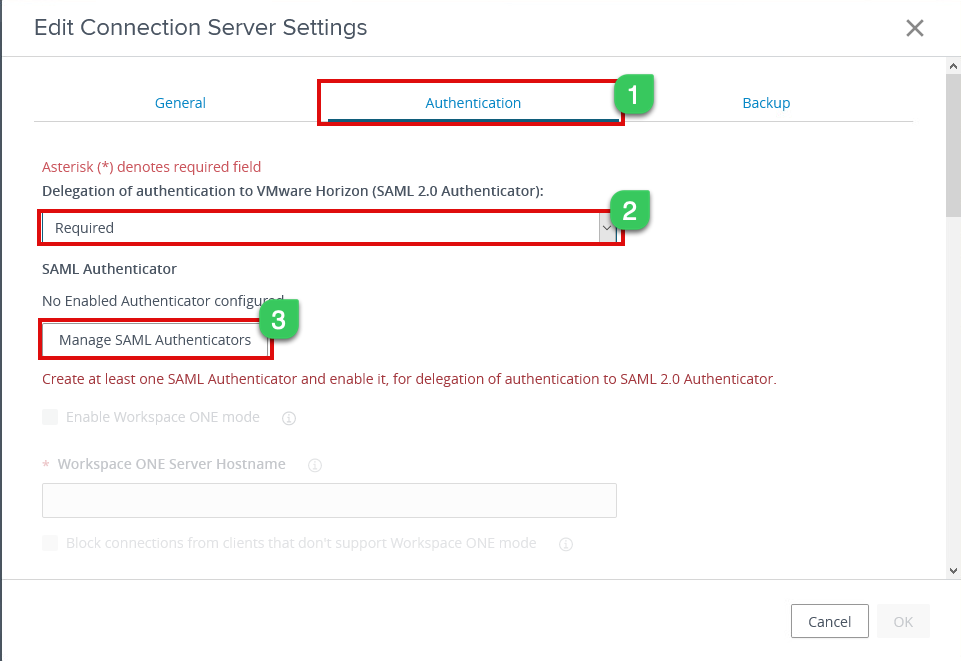
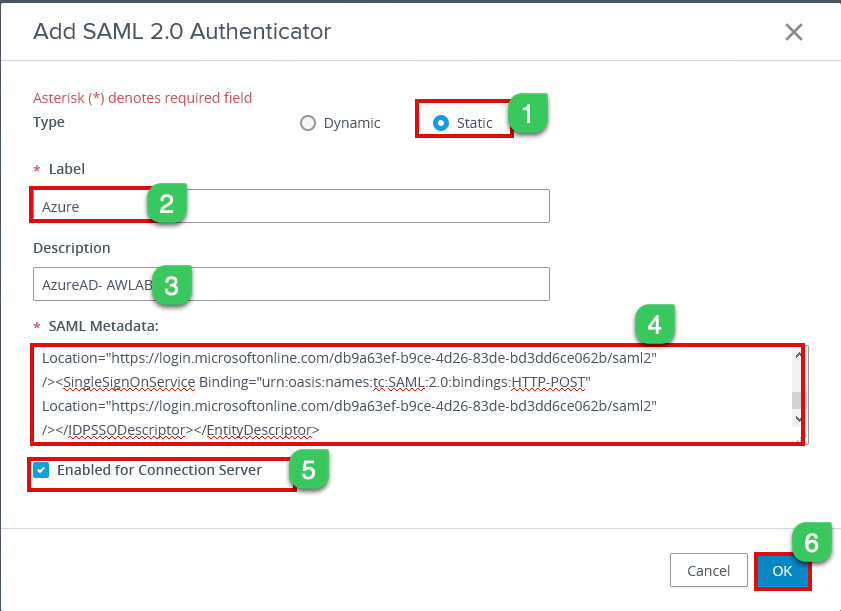
3d. Under Manage SAML Authenticator page, select Add and configure as below
Type: Static
Label: Type the preferred name for the Authenticator label
Description: Optional
SAML Metadata: Open the metadata file downloaded from Step # xx and copy-paste the metadata file in this section
Select checkbox Enabled for Connection Server and click ok to save the config.
3e. Under the connection server setting page, select the remaining connection server and enable SAML Authenticator as below
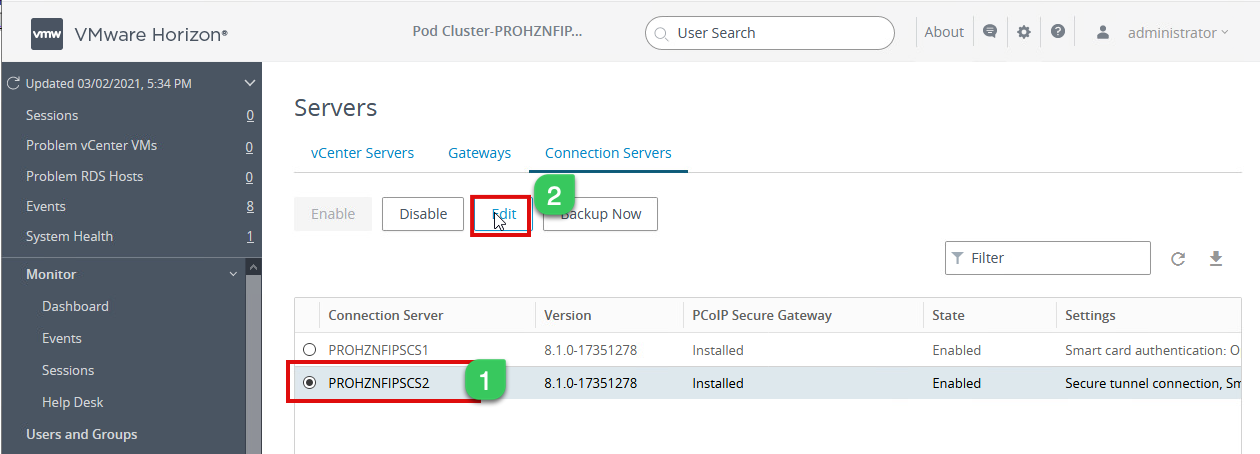
3f. Select the Authentication page and under “Delegation of authentication to VMware Horizon,” select Allowed and click on Manage SAML Authenticators
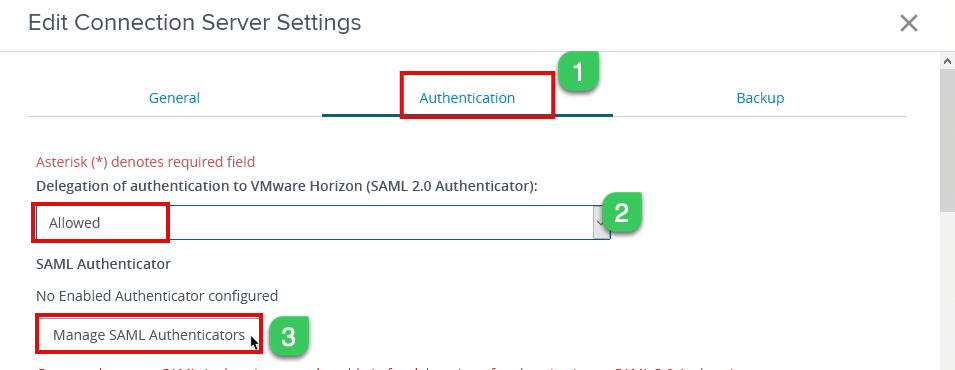
3g. You should now be able to see the SAML authenticator configured from the previous step; select the Authenticator and click edit
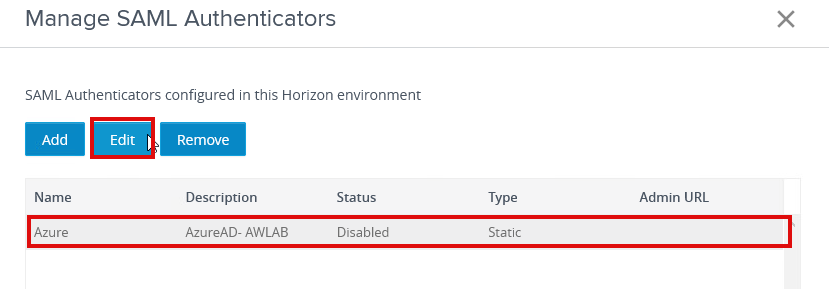
3h. All the values should be pre-populated from the previous steps, and we only have to check “Enable for Connection Server” and click ok
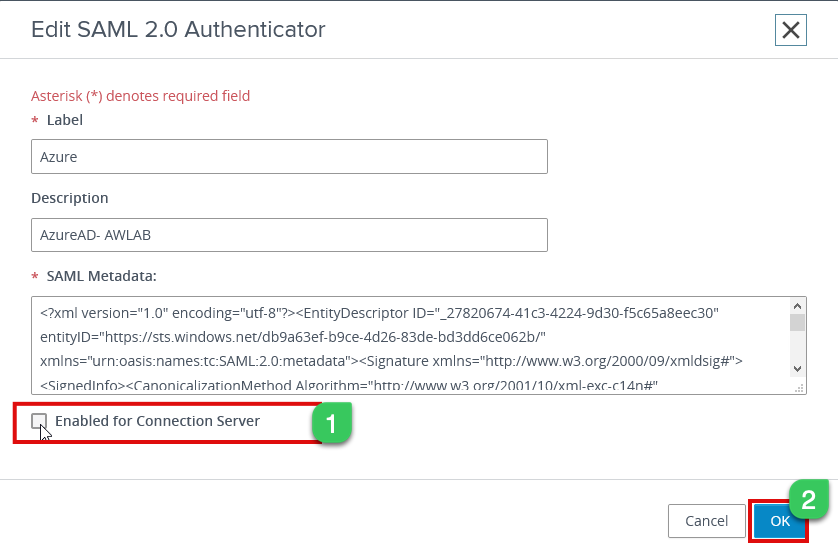
If you have more than two connection server, repeat the same steps as above and enable the remaining connection servers
3i The next step is now to enable the newly added SAML Authenticator in my setup. I name it “Azure” authenticator for TrueSSO.
Log in to one of the connection servers and open the command prompt as administrator; we will use the vdmUtil command to list the number of authenticators available and their status.
Remove the bracket from the below command uses the actual value.
vdmutil --authAs --authDomain --authPassword --truesso --list --authenticator
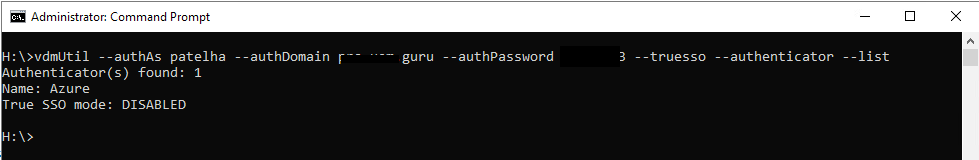
As shown above, In my lab, it finds only one Autehnicator, and staus are disabled; we need to now set TrueSSO mode enable.
3j. Execute the below command using vdmUtil to set to Enable
vdmutil --authAs --authDomain --authPassword --truesso --authenticator --edit name --truessoMode Always
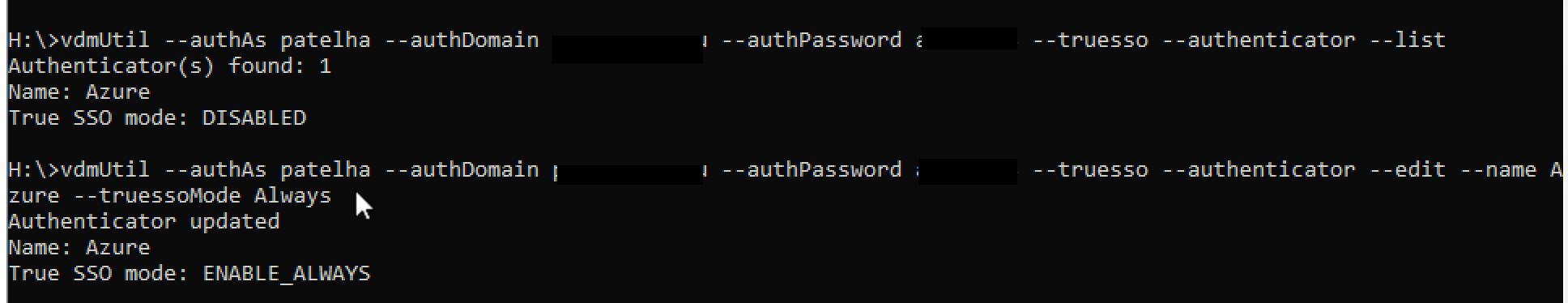
For this true sso mode, if you use –truessoMode ALWAYS, it will always use TrueSSO even if a password was supplied when the user logged into the IDP such as VMware Workspace ONE Access, Azure AD, or Okta. If you choose –trueSSO Mode Enable it will only used if no password was supplied when a user logged into IDP.
Now, we are all set for testing and validation; see below for end-to-end-user login.
Here is a quick video of the above workflow, where the user login via browser and goes directly to the Horizon URL, which will redirect to Microsoft Azure AD. Since my domain is federated with ADFS, it will redirect the user back to ADFS. My external authentication policies set at ADFS will authenticate the user. Once a user is successfully authenticated, additional Azure AD conditional policies will be applied after all the verification. UAG will pass SAML to the Connection server, and TrueSSO will create a short-lived certificate so the user can log in without any additional password prompt.